Who Has Your Back?

Download Report
Download the complete Who Has Your Back? 2015: Protecting Your Data From Government Requests report as a PDF.
Executive Summary
We live digital lives—from the videos shared on social networks, to location-aware apps on mobile phones, to log-in data for connecting to our email, to our stored documents, to our search history. The personal, the profound, and even the absurd are all transcribed into data packets, whizzing through the fiber-optic arteries of the network.
While our daily lives have upgraded to the 21st century, the law hasn’t kept pace. To date, the U.S. Congress hasn’t managed to update the 1986 Electronic Communications Privacy Act to acknowledge that email stored more than 6 months deserves identical protections to email stored less than 6 months. Congress also dragged its feet on halting the NSA’s indiscriminate surveillance of online communications and has yet to enact the strong reforms we deserve. Congress is even on the precipice of making things far worse, considering proposals that would mandate government backdoors into the technology we rely on to digitally communicate.
In this climate, we increasingly look to technology companies themselves to have the strongest possible policies when it comes to protecting user rights. Which companies will stand by users, insisting on transparency and strong legal standards around government access to user data? And which companies make those policies public, letting the world—and their own users—judge their stances on standing up for privacy rights?
For four years, the Electronic Frontier Foundation documented the practices of major Internet companies and service providers, judging their publicly available policies, and highlighting best practices. Over the course of those first four reports, we watched a transformation take place among the practices of major technology companies. Overwhelmingly, tech giants began publishing annual reports about government data requests, promising to provide users notice when the government sought access to their data, and requiring a search warrant before handing over user content. Those best practices we identified in early reports became industry standards in a few short years, and we’re proud of the role our annual report played in pushing companies to institute these changes.
But times have changed, and now users expect more.
The criteria we used to judge companies in 2011 were ambitious for the time, but they’ve been almost universally adopted in the years since then. Now, users should expect companies to far exceed the standards articulated in the original Who Has Your Back report. Users should look to companies like Google, Apple, Facebook, and Amazon to be transparent about the types of content that is blocked or censored in response to government requests, as well as what deleted data is kept around in case government agents seek it in the future. We also look to these companies to take a principled stance against government-mandated backdoors.
In this, our fifth annual Who Has Your Back report, we took the main principles of the prior reports and rolled them into a single category: Industry-Accepted Best Practices. We’ve also refined our expectations around providing users notice and added new categories to highlight other important transparency and user rights issues.
We think it’s time to expect more from Silicon Valley. We designed this report to take the basic principles of Who Has Your Back up a notch and see which companies were still leading the pack. Already, our newest report has had a similar effect on the industry as a whole, encouraging companies large and small to strive for more when it comes to standing by their users. In the months since we first told the companies what this year’s criteria would be, we’ve seen significant improvement in company practices. And we hope—and expect—that over the next year, we’ll see even more.
Evaluation Criteria
We used the following five criteria to assess company practices and policies:
1. Industry-Accepted Best Practices. This is a combined category that measures companies on three criteria (which were each listed separately in prior years’ reports):
- Does the company require the government to obtain a warrant1 from a judge before handing over the content of user communications?
- Does the company publish a transparency report, i.e. regular, useful data about how many times governments sought user data and how often the company provided user data to governments?
- Does the company publish law enforcement guides explaining how they respond to data demands from the government?
Companies must fulfill all three criteria in order to receive credit.
2. Tell users about government data requests. To earn a star in this category, Internet companies must promise to tell users when the U.S. government seeks their data unless prohibited by law, in very narrow and defined emergency situations,2 or unless doing so would be futile or ineffective.3 Notice gives users a chance to defend themselves against overreaching government demands for their data. The best practice is to give users prior notice of such demands, so that they have an opportunity to challenge them in court. We have thus adjusted our criterion from prior years. We now require that the company provide advance notice to users except when prohibited by law or in an emergency and that the company also commit to providing delayed notice after the emergency has ended or when the gag has been lifted. As we were drafting last year’s report, we let the companies know that we were going to make this adjustment for 2015 to give them a full year to implement procedures to give delayed notice when appropriate.
3. Publicly disclose the company’s data retention policies. This category awards companies that disclose how long they maintain data about their users that isn’t accessible to the user—specifically including logs of users’ IP addresses and deleted content—in a form accessible to law enforcement. If the retention period may vary for technical or other reasons, the company must disclose that fact and should publish an approximate average or typical range, along with an upper bound, if any. We awarded this star to any company that discloses its policy to the public—even if that policy is one that EFF strongly disagrees with, for instance, if the company discloses that it retains data about its users forever.
4. Disclose the number of times governments seek the removal of user content or accounts and how often the company complies. Transparency reports are now industry standard practices. We believe that companies’ responsibility to be transparent includes not only disclosing when governments demand user data, but also how often governments seek the removal of user content or the suspension of user accounts and how often the company complies with such demands. We award a star in this category to companies that regularly publish this information, either in their transparency report or in another similarly accessible form. Companies should include formal legal process as well as informal government requests in their reporting, as government censorship takes many forms.
5. Pro-user public policies: opposing backdoors. Every year, we dedicate one category to a public policy position of a company. For three years, we acknowledged companies working publicly to update and reform the Electronic Communications Privacy Act. Last year, we noted companies who publicly opposed mass surveillance. This year, given the reinvigorated debate over encryption, we are asking companies to take a public position against the compelled inclusion of deliberate security weaknesses or other compelled back doors. This could be in a blog post, in a transparency report, by publicly signing a coalition letter, or though another public, official, written format. We expect this category to continue to evolve, so that we can track industry players across a range of important privacy issues.
Results Summary: Companies Adopt Industry-Accepted Best Practices Around Privacy and Transparency and Reject Government Backdoors
Major Findings in the 2015 Report:
-
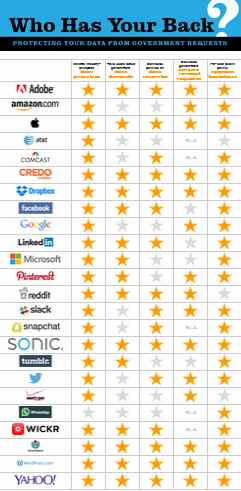
- Nine Companies Receive All Available Stars: Adobe, Apple, CREDO, Dropbox, Sonic, Wickr, Wikimedia, Wordpress.com, and Yahoo
- AT&T, Verizon, and WhatsApp Lag Behind Industry in Standing by Users
- Overwhelming Majority of Tech Companies Oppose Government-Mandated Backdoors
We are pleased to announce that nine companies earned stars in every category that was available to them: Adobe, Apple, CREDO, Dropbox, Sonic, Wickr, Wikimedia, Wordpress.com, and Yahoo. (Note that some companies host little or no content, and thus the transparency about government data removal requests may not apply to them.) These nine companies show that it is practical for major technology companies to adopt best practices around transparency and stand by their users when the government comes knocking.
Unfortunately, not all companies are embodying such forward-thinking practices. Two major telecoms—Verizon and AT&T—received especially poor results, thus continuing a trend we identified in prior reports where many large telecom providers fail to keep pace with the rest of the tech sector.
Notably, some companies that act as Internet service providers and general telecommunications providers are leading the way in adopting strong policies in defense of user rights. In particular, CREDO and Sonic again received credit in every category EFF rates. Comcast is close behind, earning an impressive 3 out of 4 possible stars. We hope other telecoms can rise to these standards in the coming years.
We added three new companies to this year’s report: reddit, Slack, and WhatsApp. All three were responsive to conversations with EFF, and reddit and Slack have fulfilled several of the criteria to earn stars, though neither received credit in all available categories. Despite being given a full year to prepare for its inclusion in the report, WhatsApp did not fare so well. WhatsApp earned credit for its parent company Facebook’s public policy position opposing backdoors and nothing else.
It is also clear that the technology industry stands united against government-mandated backdoors. Twenty-one of the 24 companies we evaluated have public statements opposing backdoors, which weaken security and endanger user privacy. ISPs, cloud storage providers, webmail providers, and social networks are overwhelmingly aligned in rejecting government-mandated security weaknesses.
Industry-Accepted Best Practices
These standards were developed over the course of four years of EFF reports, and they encompass three of the main issues at the heart of Who Has Your Back: requiring a warrant before handing over user content, publishing regular transparency reports, and publishing law enforcement guides. The transparency reports and the law enforcement guides help users understand how often and under what circumstances the companies are responding to government data requests, while the warrant for content ensures a strong legal requirement be met before data is handed to law enforcement.
In 2011, no company received credit in all of these categories (or even in two of those categories, since in 2011 we didn’t include a category for requiring warrants for content). This year, 23 of the 24 companies in our report have adopted these principles. It’s clear that these best practices truly are accepted by the technology industry. WhatsApp is notably lagging behind.
Notifying Users of Government Requests
This year, we asked companies to do more than simply promise to inform users about government data requests. We also asked them to provide advance notice to users before handing the data to the government. In cases when companies are prohibited from doing so, we asked the companies to promise to provide notice after an emergency has ended or a gag was lifted. Because we knew it would take significant engineering and workflow changes for some of the larger companies to implement these practices, we gave them more than a year’s notice that this criterion would be included in the 2015 report.
Two companies who had previously earned credit in our report for telling users about government data requests did not receive credit this year because they did not have policies that tell users after a gag has been lifted or an emergency ended: Google and Twitter.
Fifteen out of the 24 companies we evaluated did meet this stronger criterion, and we’re pleased that the industry is evolving in this way.
We were particularly impressed by the strong policy adopted by Dropbox, which states:
Dropbox's policy is to provide notice to users about law enforcement requests for their information prior to complying with the request, unless prohibited by law. We might delay notice in cases involving the threat of death or bodily injury, or the exploitation of children. It is our policy to provide notice to users about grand jury subpoenas seeking user information. If you object to the user receiving notice in a particular case, please provide legal justification when serving the subpoena or obtain a sealing order prior to service. Once the basis for the non-disclosure has expired, we will give notice to the user.
Disclosing Data Retention Policies
For the first time this year, we evaluated companies on whether they were transparent about what deleted data they stored. Often, users may not realize that data they delete from an email service provider or off a social network is still stored and available to law enforcement agencies upon request. Transparency is the first step to educating users about what happens to their deleted data, so we are evaluating companies on their transparency practices in this category. Note that we aren’t making specific requirements about a company deleting data after a certain time. Indeed, some companies publicly state that they maintain deleted data and server logs indefinitely—a practice we think is terrible for users. However, for this report, we’re just asking companies to be clear about retention periods for data collected that may not be easily viewable to the user (including IP addresses and DHCP data) as well as content that users deleted.
Fifteen of the 24 companies we evaluated received credit in this category. We were particularly impressed by the clarity and detail of Comcast’s disclosures:
Comcast maintains personally identifiable information about you in our regular business records while you are a subscriber to our cable service or other services. We also maintain this information for a period of time after you are no longer a subscriber if the information is necessary for the purposes for which it was collected or to satisfy legal requirements. These purposes typically include business, legal, or tax purposes. If these purposes no longer apply, we will destroy, de-identify, or anonymize the information according to our internal policies and procedures.
as well as:
Comcast can provide historic Internet Protocol assignment and session information for a period of 180 days for Xfinity Internet users.
and
Customer deleted emails remain in the customer’s Trash Folder for 30 days if the folder is not emptied. Once emptied, the customer can retrieve those emails for 15 days via the “Recover Deleted items” folder under the Trash header. Xfinity Internet customers can set their own preferences for certain web mail deletion or retention. Thus, depending on a customer’s deletion settings, Comcast may, or may not, have responsive information to a request for email information.
and
Comcast maintains historical call detail records for our Xfinity Voice telephone service for two years. This includes local, local toll, and long distance records. In limited instances, older records may be available, but will require additional time and resources to retrieve.
Comcast has other details available in its Law Enforcement Handbook.
Disclosing Government Content Removal Requests
For more than a year, EFF’s lead investigative researcher Dave Maass has been reporting on how Facebook cooperates with prison systems across the United States to block prisoner access to the social network. Facebook had even set up a dedicated “Inmate Account Takedown Request” form to help prison officials quickly and easily flag prisoner-run accounts for suspension, even when the accounts did not violate any of Facebook’s terms of service.
This practice was the inspiration for EFF’s newest category: tracking how often companies are removing content or shutting down accounts at the behest of the government. To earn credit in this category, companies need not refuse all or even any government content removal requests. Rather, they must simply be transparent about how often they are blocking or removing content or accounts.
Though this is simple enough, many companies are falling short in this area including Facebook, the company whose practices inspired the creation of the category. Fifteen out of the 24 companies we evaluated received credit in this category, though several do not host content and so this category did not apply to them.
A particularly strong example of this practice is the data published by Twitter, which includes an interactive map that allows users to mouse over countries and get details about content removal requests over a six-month time period.

Pro-User Public Policy: Opposing Backdoors
One of the big trends we’re seeing across the tech industry is a rejection of government-mandated security weaknesses. In fact, 21 of the 24 companies we evaluated took a public position opposing backdoors. This is a powerful statement from the technology community that Congress and the White House should heed.
Many of the companies signed onto a letter organized by the Open Technology Institute that opposed mandates to intentionally weaken security, which stated:
We urge you to reject any proposal that U.S. companies deliberately weaken the security of our products… Whether you call them “front doors” or “back doors,” introducing intentional vulnerabilities into secure products for the government’s use will make those products less secure against other attackers. Every computer security expert that has spoken publicly on this issue agrees on this point, including the government’s own experts.
Conclusions
We are pleased to see major tech companies competing on privacy and user rights. Practices that encourage transparency with users about government data requests are becoming the default for companies across the web. While we’re only able to judge a small selection of the tech industry, we believe this is emblematic of a broader shift. Perhaps invigorated by the ongoing debates around government surveillance and in response to growing public attention around these issues, more and more companies are voluntarily speaking out about government data requests and giving users tools to fight back.
We think that this type of transparency can help prompt broader discussion and systematic change about how and when governments access user data and perhaps eventually prompt Congress to clarify and improve the privacy laws for digital data. We also recognize that technology companies are in a position to know about and resist overbroad government requests, so we need to do everything within our power to encourage them to speak out and fight back. In handing our data to these companies, we’ve handed them a huge responsibility to do what they can to stand up for privacy. We’re pleased that many of the companies we evaluated are stepping up to the task.